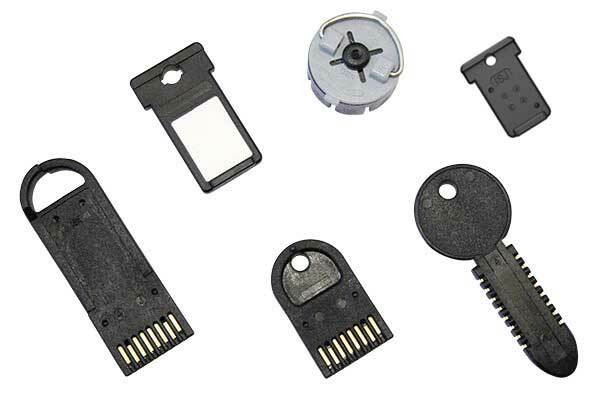
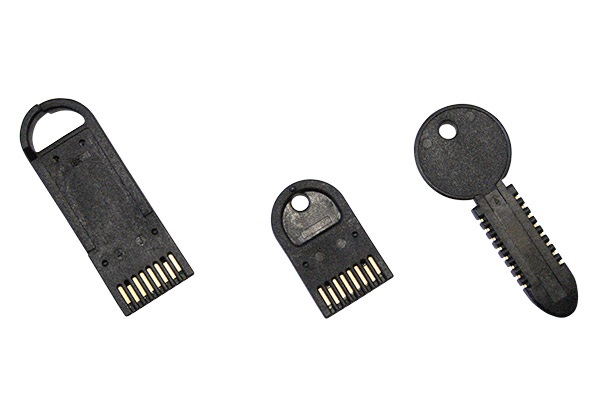
Portable memory for any application
Simply put, there are two main uses for portable memory: As a credential - a device is used to ID/authenticate a person/device For data transfer - a device is used to move data from here to there for a variety of specific applications.
Support & Resources
Visit our Resources page for white papers, FAQ articles to learn more about Wireless coexistence, Crypto Ignition (CIK) implementation and comparing consumer and OEM portable memory.
More Rugged. More Reliable.
Our products meet the requirements of the most demanding applications and can withstand up to 50,000 insertion/removal cycles. They are chemical and ESD resistant, and deliver unmatched performance in extreme environments.
Long-term Availability
OEMs count on our products to be available and supported for the lifetime of their programs. In fact, some of our products have been available, unchanged, for more than 20 years.
Unique & Familiar Form Factors
Our proprietary-shaped products are intuitive for end users. When our key or token becomes an integral part of your product’s identity, it opens up a new revenue stream for you. Other devices do not fit in our unique receptacles, providing an added level of security.
Fully Engineered Systems
Our full catalog of memory keys/tokens and receptacles gives you a cost-effective way to incorporate a high performance memory device in your products. Want to lower your R&D costs and reduce your time-to-market? Check out our full line of development kits and support peripherals.